Overview
Symantec Endpoint Prevent for DLP has the ability to track and limit data being copied to removable storage (USB drives, etc.). Within a DLP policy we can leverage the DeviceID of a removable storage device as either an inclusion or exclusion to our policy. This document will cover how to set it up.
Process
The first tool we need to leverage is “DeviceID.exe” which is a part of the Tools folder under the DLP agent source directory. This executable will allow us to gather both the Device ID and the Regex that is needed for either the exclusion or inclusion.
This information is taken from the Help file for DLP and the DLP Admin Guide.
- Connect the USB Device to your computer
- From the command prompt navigate to the folder where the “Tools” directory is located
- Execute “DeviceID.exe” to get a list of the devices attached to your computer
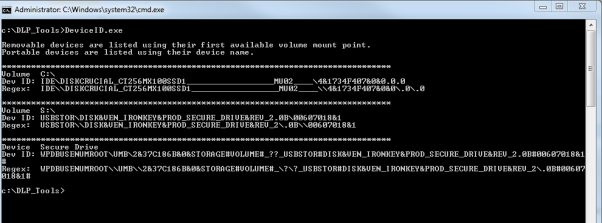
- There are two values displayed per device connected to your laptop/desktop
- Dev ID: Contains the full string for the device connected to your laptop
- Regex: The value we want to put in our exclusion or inclusion
- NOTE: If you have a large amount of devices attached to your laptop or desktop the output can be directed to a text file via “DeviceID.exe > textfile.txt”
- Open up the DLP Console and navigate to System -> Agents -> Endpoint Devices
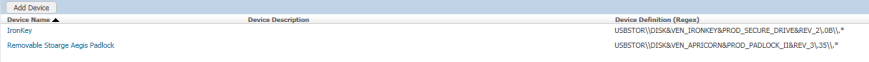
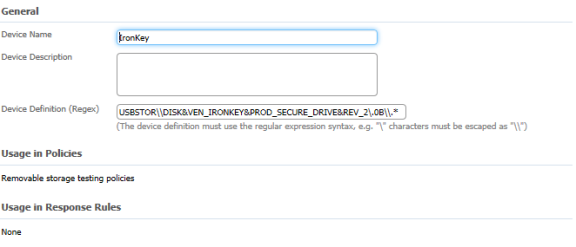
- Select “Add Device” and fill out the form
- Note: Use the Regex value from DeviceID to fill out the device definition portion of things
- NOTE: The goal is to be both as generic and specific as possible to make sure there is not a giant list of device ids
Leveraging the DeviceID in a DLP Policy
Once the DeviceID is created it can be used as either an exclusion or an inclusion within the policy
- Login to the DLP Console
- Navigate to Policy Portion (Policy -> Policy List)
- Edit (or create) the policy you would like to use this in
- Select “Add Exception”
- Towards the bottom of the Exception Type is “Endpoint Device Class or ID”
- Select this option and select “Next”
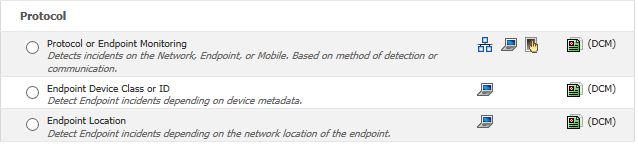
- Select the DeviceID you would like to use for an exclusion and select next
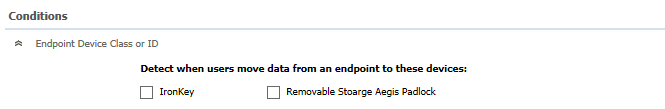
- Select “OK” to save your exception
- Towards the bottom of the Exception Type is “Endpoint Device Class or ID”
- NOTE: This same process can be used to create an inclusion in your DLP Policy as well







You must be logged in to post a comment.